by Mourad Ben

The road to hell is paved with good intentions. I never thought much of that saying growing up. My dad was obsessed with post-apocalyptic worlds. He would recount stories to my brothers and I, of a world before our existence radically different from ours. I never understood what he meant. Every time I went online to read, or went outside to observe, the world seemed just as it did in his stories. Supermarkets, universities and hockey rinks existed; people had jobs, goals, ambitions. They were free to do what they wanted. Sure, computers have become faster; the internet is more accessible, information is more easily disseminated. But, day to day life, through my eyes, is no different from what my dad experienced. So why does he insist that our world is so different? Why does he call what happened on that day an apocalypse? In proportion to other historical episodes, the events of that day seem small. Why was this the event that changed the world more than any other?
Table of Contents
In the beginning
The story began, as many do, on a university campus. Two brilliant computer scientists dedicated to developing their own search engine. The ideas that underly their algorithms are not particularly relevant to our story, except for the fact that they were motivated by the credo: Move fast and break things. Why bother thinking them through? The world is not deterministic. Don’t waste time mulling over the details! Who cares anyway? First place is all that counts… Right?
Their technology focused on exactly what it purported to do: Search. Why should they care about security? Why should they care about transactions? What does that have to do with what they are trying to achieve? Well, as it turns out, everything.
In the next two decades, these two scientists and their company would go on to create an array of products that changed how people interact with each other. How they do business, spread ideas, cure disease. Everything about life was changing. At the beginning of high school, I thought this was what my dad meant by life being different. However, every time I brought it up, he’d simply laugh and tell me how I am not yet able to understand. According to him, I was too dependent on the system. With an almost patronizing smirk on his face, he would say: “Not until someone else builds something that solves these problems, will you have understood the very nature of these problems and their true cost”. I hate when he’s like that. I am not stupid. I know I can get it. Why does he not just tell me? Happy to talk my ear off about how the world as he knows it is over but refuses to tell me why. What’s so wrong with what they have accomplished? I have access to an email service for free! A browser for free! Spreadsheets, word processors, music, videos, books all free! What’s so wrong with that? Think about it. Anyone in the world can now work with other people and scale their creation to millions, instantly! How is that a bad thing? He only ever had one response and I still don’t fully understand it: The argument comes from a logician and mathematician named Kurt Göedel who proved that there can be no human construct or system of thought that does not rely on some reality outside itself.
The contradictory economics of free
Growing up with two brothers introduced me to what would eventually become my area of expertise: Economics. Specifically, I learned first-hand about the ideas of sharing, zero sum and positive sum games. I always thought it was interesting how people divided themselves according to certain properties they exhibited. As a result, one group was often more entitled to somethings than others. My brothers, for example, were older than me, so it follows: They get the new bikes; I get the hand me downs. They get the new clothes; I get the hand me downs. It took me a while to work out the formal notation, but as I understood it: They get to choose what they want, and I have to like it. It was not an optimal system, but it worked! As a family, we were constrained financially. Having the ability to pass down tools meant that, technically, my bike and my clothes were free. However, as a teenager, I questioned that premise a lot. Sure, it might seem like it’s free, but the cost was just shifted through time. Things still had to be paid for. Free makes no sense… If things were truly free such that someone puts in energy toward creating something, then simply gives it away, that person would not survive long enough to produce more for everyone. What’s more, no one considered the other costs that I have to bear: That of a rusty chain, squeaky gears and an outdated flame design that was more likely to get me beat up at the park then it was to help me win a race. But at least there’s an upside: I don’t have to worry that someone will steal my bike!
As a teenager, this was the argument I used to rationalize what it meant to get something for nothing. How could free be a bad thing when it leads to my being able to enjoy myself? I remember bringing this up to my dad once and his response was: “Free is a lie” and continued by quoting an economist named George Gilder, explaining that a price of zero signifies a return to the barter system, a morass that the human race left behind in the stone age. As I got older, I’d often question his response. How can something being free be dragging us back to the stone age? What does one have to do with other? It was not until I started self-learning about economics in my free time that I realized what he meant: Free avoids the price system and the requirement of security. I guess what my dad was trying to say was that if I am okay with receiving an old bike, does it really allow me to enjoy myself? Clearly the answer is no, at least, not in an optimal way relative to my siblings. What’s worse, I have come to realize that it’s not only a detriment to me, but to everyone. What I mean is: If a business produces bikes that survive a long time in the market, it relieves the business of the burden of constantly having to improve their technology and is actively prohibiting them from learning. One of the most important ideas I would read about in my spare time came from George Gilder who wrote: “The key to our capitalist system is learning curves. Wealth is knowledge and economic growth is learning. One of the crucial instruments of learning in a capitalist system is the signal of prices. By giving me a product because its free, [my parents are actively encouraging a business] to avoid this precarious process of falsifiable learning which is at the heart of capitalist growth. [By not paying for a new or better product and contenting themselves to give me something for free], they [are giving businesses carte-blanche to] avoid the learning challenge to a great extent. They avoid direct responsibilities to customers, and they avoid the learning process that allows for capitalist growth”.
As it turns out, forcing me to accept the hand me downs from my siblings is not only hindering my experience riding that bike; it also prevents these commodities from becoming better, lighter, cheaper and faster. Free as it seems, bottlenecks the innovation process. At the time, this single thought kept me awake at night. How can this be? How am I supposed to reconcile the fact that my family cannot afford to buy new products for all their kids, while also knowing the negative implications of their actions? They know that these businesses will not be held accountable. They know that their micro-economic decisions have broad impacts on the rest of the world. They know it, and they’re okay with it, while simultaneously not being okay with it. An obvious contradiction, yet all of us willingly accept it and businesses encourage it!
This behaviour is endemic to how the technology economy works today because learning is not a mechanism that is integral to business models. Technology companies and related businesses know that there is no way of linking the implications of their actions to the possible consequences. There is no ground truth, nothing to uniquely identify a business, a person and their interactions as well as the resultant consequences. It is a free-for-all that allows people and businesses to behave in a way that is not to each other’s benefit. In this case, the business continues to produce bikes that people keep far beyond their lifetimes. Therefore, businesses sell bikes and people’s ability to benefit from them diminishes over time. There is nothing to quantify my loss of enjoyment, therefore, no incentive for businesses to improve the product they create. Yet, I am still better off financially for having used the bike. This example, although trivial with respect to bikes, magnifies exponentially when discussing software which can scale to millions instantly. This nuance was lost on me in my youth but growing up in the age of technology has made me keenly aware of this problem.
The elephant in the room
Today, my brothers and I know all too well that the learning process in information technology is a joke. Just consider security and privacy for second. You cannot go anywhere online without someone or something knowing who you are and tracking what you are doing. Every day, I get an alert in my free email, while using my free browser that says: Did you attempt to sign in from this location at that time? Was this you? Please enter your password to confirm. Oh, forgot your password? That’s okay, you have previously associated your work email to this one.
During my economics degree we learned that there is no manna from heaven. My professor would ramble on for hours at a time: “If I am able to create an account for free to buy or sell goods, to contact my friends and loved ones; I have not actually done so for free”. This makes no sense! After all I did not pay for the service, but come on, I just replied to an email this morning and my bank account balance is still the same. How does that work? Where is the money coming? As it turns out, these businesses are not doing anything for free. They are taking advantage of the process that kept me awake in my youth. They know that people are self-interested and constrained by their financial means. So, given a choice between a paid product and free product that does the same thing, they will choose the free product. In the context of technology, specifically software, the problem become more obvious: Businesses can offer products that their end users can use for free. However, this is not the same as being free. These products do come at a cost, but this cost is not paid directly by the user which provides an illusion that the product was free.
This so-called system of the world is what I have started to suspect my dad refers to as the apocalypse. No body likes not having privacy or security; yet, we accept it. I can’t believe it, I don’t want to believe it. We accept it as if it were no more than a cost of doing business. We accept it as if it were akin to needing oxygen to continue to live. We accept it as if we must give up any semblance of security or privacy to even be able to benefit from information technology. I think my dads fears about the apocalypse are starting to sound less unfounded by the second. As i’ve understood it, his hope is that one-day people would realize this notion of free is not real. That it is not good or to their benefit. That something must be done. But what?
No individual can hold these businesses accountable as the services they use are tremendously valuable to the individual, and the cost paid for the product cannot be linked from the user to the business’s bottom line. This is because we are their product, or rather, our privacy and security are. They cannot be held accountable when we are actively incentivizing them to continue. Worse yet, we are starting to see that this practice is not only slowing the innovation of products produced by these companies, but they are also slowing the individual’s ability to produce value altogether. All of the information that is needed for people to better understand how to improve any process or product is being swallowed up and siloed by big businesses. The benefits individuals gain from using their services is marginal relative to what is being lost to this system of the world. This is not a win-win situation. At best, it is a pyrrhic victory. Individuals can no longer participate in the economy by producing their own solutions, and big businesses continue to benefit at the expense of the individual.
As it turns out, “free” slows down everyone involved. The businesses are not incentivized to produce better products, and the individuals do not have access to the information and data they need to solve problems and produce new solutions. This system is antithetical to innovation. Human intelligence is distributed across the world, yet the information needed to identify and solve problems is isolated within large businesses. In short, we are incentivized to not interfere with their system of the world, while their system slows down and prevents much needed solutions. As new problems arise, people do not have the tools they need to solve them. The only way to get around this would be to re-design the entire system of the world to be centered around the individual. The information individuals need to be able to solve problems as they arise should be distributed.
Only after these realizations did I finally start to understand what Kurt Göedel meant when he said there can be no human system of thought that does not rely on some reality outside itself. It is not possible for the economy to continue growing given these conditions. Information cannot be siloed. It must be available to everyone. But how can we create a system that centers around the individual while providing as much value as businesses do when they offer “free” products? Mentioning this to my dad he exclaimed: “You have to start from the beginning. You cannot move fast and break things. You must create a system which has, at its core, the individual. After all, It is the individual who creates”. For the first time in my life, my dad was not answering with a bromide, but rather he began to explain the solution to the apocalypse: A new system of the world.
His idea is that security and privacy will be so fundamental to this new system that its very name will be derived from it: The Cryptocosm. He continued by explaining that “in the Cryptocosm, privacy and security is not a procedure or mechanism; it is an architecture. The new system of the world must begin by defining the ground state, and the ground state is you. In this Cryptocosm, a fundamental technology called the blockchain will permit individuals to have a unique identifier which is as unique to us as our DNA. It allows you to keep your private information to yourself while distributing information across the network just as human intelligence is distributed across the world”. Nodding my head I thought, this means that individuals will no longer need to petition the businesses for the right to benefit from a technology. Rather, with the right information in the right hands, these tools can be created in a way that incentivizes their maintenance by individuals. These tools and their monetary benefits will no longer incentivize a system of the world that actively bottlenecks development. These tools will no longer be marginally beneficial to users and overwhelmingly beneficial to big businesses. Rather, these tools will more equitably benefit their creators and the users. At first glance it seems this thought only leads to a new contradiction: How is it possible to uniquely identify an individual using private information, while simultaneously distributing that information around the world? Asking my dad, he laughed as he replied: “this is not a contradiction, but rather a cryptography problem. Sit down and I will explain.”
Being private while in public
My dad looked at me nodding his head and started by saying: “You are beginning to understand why I call it an apocalypse. The current system of the world will grind all innovation in information technology to a halt. There will be no need for anyone to do anything other than what they are doing today. There is no incentive for businesses to change it, and no means for individuals to do so either. So how do we address the elephant in room? How do we create a private identifier that can be shared with others while also preventing it from being public”? The answer, he explained, “is through a cryptographic tool called a hash. A hashing function is a special type of function. Similar to what you have seen in math class. It is an input/output machine but with three special properties: First, it is a one-way function. This means we can take some data, hash it, and will never be able to go backward. Meaning, we cannot take the hash, and extract the original data. For example, I can take some data like the string “hello world” and pass it through the SHA256 algorithm. SHA256 (Secure Hash Algorithm returning 256 bits) will produce”:
b94d27b9934d3e08a52e52d7da7dabfac484efe37a5380ee9088f7ace2efcde9
He continued, “by its one-way property, it is almost impossible for an individual or a group of individuals to derive a function that will take the above hash as input and produce “hello world”.”
The second important property of hash functions, he explained, “is the “chaos” built in. For example, one might think if hashing “hello world” produces the hash we just saw, then perhaps hashing “helloworld” would produce a similar hash. After all, the only difference between the two is a single space. However, this is wrong. Even a seemingly insignificant change results in a drastically different hash”. Pausing to write some code on his computer, “consider the two hashes below, the first is a hash for “hello world” and the second is a hash for “helloworld”. Clearly they are very different from one another.”
b94d27b9934d3e08a52e52d7da7dabfac484efe37a5380ee9088f7ace2efcde9
936a185caaa266bb9cbe981e9e05cb78cd732b0b3280eb944412bb6f8f8f07af
He continued, “the third important property is that hashes can be considered as a unique representation of data. If I take variables and produce their hash, only those same values will ever produce that hash. Even an insignificant change, as we’ve just discussed, will produce a different hash. So, we are able to take data, hash it, and make sure that it is unique. Comparing it to a previously stored hash we already know contains our information allows us to ensure no other modifications have been made. These three properties will play a pivotal role in our new system of the world since they are how we will create a blockchain. Linking these hashes in a linked list data structure allows for the blockchain to exist. It ensures that each block is connected to the previous by a hash which represents information that cannot be changed. This allows us to create a record of huge amounts of data through time and ensure it has not been modified. By distributing it to everyone on our network, we simply need to check that our linked lists are the same. By doing so, we know there exists a verifiably true set of data, and that to be able to modify this true dataset, one would need to modify every version of that blockchain in existence.”
Taking a second to process I respond, “so by hashing information, the original information stays private for me, but can still be made public without others necessarily knowing it or being able to extract more information about me?” “Yes”, my dad replied, “that’s exactly right. We start with a private key, this is your unique ID. We then produce an address that others can refer to in order to identify you. We can then move that information, in essence, transact, in a way that allows that data to be made public, while not explicitly referring to you, or your private key.”
Rummaging through his desk, he found a piece of paper on which he scribbled a simple diagram. He continued; “this is an example of the mechanism that allows you to produce an address from your private key. Your private key remains private, while giving you an address that can be made public. This address also has important features built in to allow other to validate that it is a real address.”
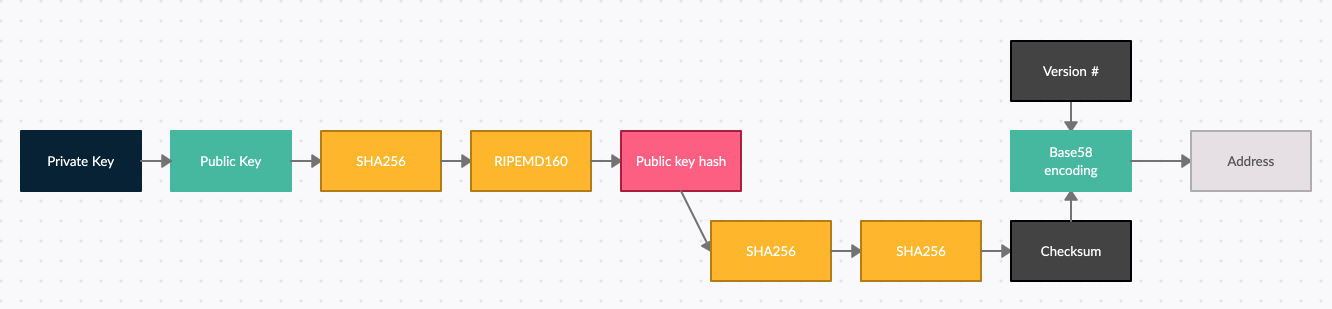
“Wait!” I exclaimed, “I still do not really understand the point of an address or how we know it is a real address”. Let me put it this way, he said, “an address serves several purposes, but perhaps the most useful for the average user is to ensure that they are transferring information from one address to another and to ensure they are transferring it to a real address. To verify that an address is “real” we use a checksum. The point of a checksum is to hash over a copy of our public key hash and take the first 4 bytes of the resultant hash. We then concatenate the public key hash with our checksum. This is useful because anytime a user writes the address of another user, we can simply remove those 4 bytes, apply the hashing again and derive the checksum anew. If the two are the same, we know, at the very least, that the address the user is trying to send information to is in fact an address and not just an arbitrary string that will lead to nowhere”. He continued, “It is important to note however, that although the checksum is useful to validate that an address is in fact an address, it is not in any way designed to verify that the address corresponds to a specific person. What this means is that as long as I keep my private key private, if anyone wants to send me information directly, they can use my address. I can prove I own that address by meeting them in the middle: I can undertake the hashing we saw in my diagram all over again to produce a public key hash, while you can decode the address until you get to the public key hash. We will literally meet in the middle!”
“Okay, so what?”, I respond, I have a piece of private and public information. How does this solve anything? “Be patient”, he replied, “we will get there. So far, we have understood that it is possible to identify a person with an address, and that only that person can prove they own that address. Let’s now consider how the blockchain works, and how this address is relevant to blockchain technology using an application of the blockchain called cryptocurrency.”
The blockchain and cryptocurrency
“I know this will be a lot but bear with me”, he said. “Let’s talk about what a blockchain is”. Pulling up his phone, he starts reading from wikipedia in a monotone: “a blockchain is a trust-less and fully decentralized peer-to-peer immutable data storage that is spread over a network of [nodes]”. Noticing my facial expressions, I believe it was at this point he must have thought he was teaching integral calculus to a gibbon because he sighed and continued: “Alright, that was a lot to process, so let’s break it down into its component parts. Just keep in mind for now, that a blockchain is a record or database that cannot be changed. It can contain information that can be used to demonstrate a pattern of behaviour or links between people, and we can call those links: Transactions”. Rhetorically, my dad asked, so how does this work? “Well, a blockchain, much like the name suggests is a chain of blocks. Each of these blocks contains information in the form of transactions. We can provide a cryptographic proof that these transactions have not been changed through the use of a Merkle Root.”
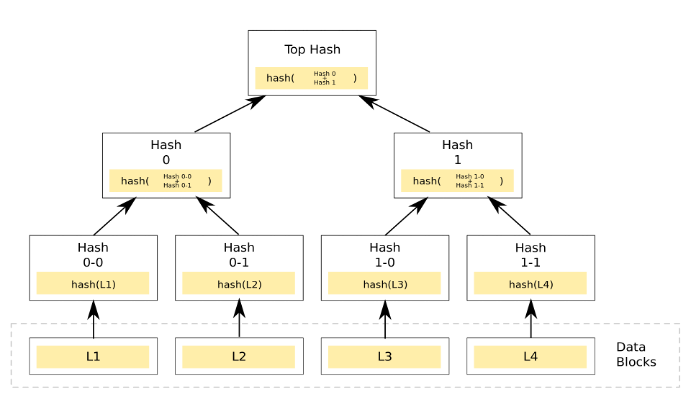
Drawing a diagram on a piece of paper, he continued to explain: “Notice the top hash of our diagram. This is our Merkle Root. The Merkle root of the block is a hash that represents the transactions that exist in that block. In our diagram, transactions are represented at the bottom as L1 through L4. We can calculate the Merkle root by first taking a set of transactions (preferably of size ) and lining them up in an order. The transactions are then paired, and each of these pairs are passed through a function to produce a corresponding hash. This is done for all pairs. Assuming you have
transactions available, pairing transactions in groups of two will not be a problem. However, if you are missing a pair, we have developed clever techniques to fill in the missing data. The process of combining the hashes of pairs of transactions allows us to produce the Merkle root. This process can be recalculated by anyone who wants to verify that a particular transaction exists in a block.”
This idea underpins how we transmit information over the blockchain. If everyone has a copy of the blockchain on their computers, everyone is able to see all transactions that occur. Everyone has a record of the transaction, its origin and its destination. We do not know who owns the keys associated with the origin and the destination, but we know that the transaction occurred. The more transactions that occur, the better peoples understanding on the links between people and businesses. If we understand those links, then we are able to understand the system itself. It is no longer in the hands of a small few, but in the hands of everyone.
Without pausing, he continued: “We know the blockchain is made up of linked blocks and each of these blocks contains a history of transactions. These linked blocks are linked by first taking the Merkle Root of the current block, referencing the hash of the previous block in the chain, and hashing these two pieces of information to create the hash of the current block. This hash will in turn be included in the next block and so on”.
Taking a second to think about it, I ask: “If each of these blocks relies on the hash of the previous block, what is hash of the first block? What are its transactions?” Without a second of hesitation, he answered: “This is the genesis block. It is a special case and is too nuanced for our explanation, it suffices to say that it is created at the beginning and serves a catalyst for our reaction”. So, the hash of the previous block allows us to build a chain as each block we create points to, or put differently, contains, the hash of the previous block. This chain allows us to validate that each block has the same information that it had when it was originally created. As a result, it is not possible to alter the contents of one block without also having to change all of blocks that come before.
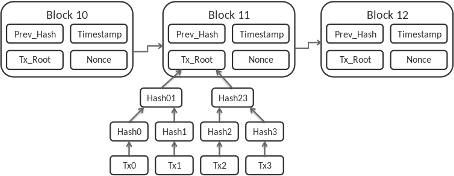
I immediately grab a piece of paper and start drawing a model. “Okay, I think I am starting to understand. Each block contains information, and an individual block cannot be altered without altering the rest of the blockchain. Since the blockchain exists on many different computers around the world, to change a blockchain, would require not only changing one blockchain, but all of them?” Yes! Exclaimed my dad. “That’s exactly it! And the best part is yet to come! See, in order to actually make sure that the blockchain works, we cannot just let anyone push whatever information they want to it. These blockchains have to talk to each other and achieve a sort of consensus. In order to do that, we will use a consensus algorithm”.
Without skipping a beat, he dives straight into an explanation of consensus algorithms. “Intuitively, what do you think can go wrong when a bunch of computers around the world are trying to agree that a new block is, for lack of a better term, “real”?”
Well, I stutter, “I know that when I play videogames online, and my connection is not very good, my game starts to lag. It shows me being somewhere on the map that does not correspond to the place I am expecting to be. I also know that sometimes people cheat, is that what we mean by ‘real’?”
Yes! He responds, “That’s right! What we are really trying to do is understand fault-tolerance. Issues of fault-tolerance arise from various sources: For example, Nodes being turned off, nodes sending improperly formatted codes or nodes sending malicious codes. So, in order to be able to figure out if any new block is real, what we are doing is trying to achieve consensus with people around the world who we don’t personally know and don’t trust. If a critical mass of people agree that a new block is ‘real’, then it is accepted by the network. Because it is in fact possible for someone to alter a decentralized blockchain by pushing a fake block to the network, a consensus algorithm prevents them from doing so with impunity. Each consensus algorithm has its own take on the how but the why is the same. For example, one must expend a lot of compute power in the proof of work consensus algorithm. Meaning, an individual actor will have to be able to compute hashes faster than everyone else on the network combined in order to have the network accept a false result.”
Nervous, I reply, “I don’t think I fully understand what you mean. Can you explain in more detail how proof of work actually works?” Pointing to the diagram I drew; my dad adds some new information to it and explains: “In order to create a block, you need to first mine it. This is a process of taking the contents of the block and hashing them. Now, do you remember that second property I talked about with respect to hashes? If I make so much as a small change to the information in the block, the resultant hash will be different. You may have noticed I added a “nonce” into your diagram. The nonce is important as we are not just looking for any old hash. We are looking for one that satisfies a specific criterion. In the proof of work consensus algorithm, this criterion is defined as a hash which begins with a certain number of zeros. The more zeros are required the more difficult or time consuming it is to find the hash. We can use this difficulty property to manipulate the network into producing a certain number of blocks over some time. As individuals are mining blocks, every time they produce a hash, they check if it satisfies the criterion requiring a certain number of zeros. If it does not, we increment our nonce value and recalculate the hash. We repeat this process until we produce a hash that satisfies our criterion. So, by making a hash sufficiently difficult to mine, we can not only throttle the number of blocks mined, we can make sure that no single actor will be able to overpower the network in aggregate and write whatever information they want to the blockchain.”
You’re going too fast! I exclaimed; can you please summarize? Smiling, he said: “What matters is that we are able to, as a group, who have never met each other, and do not trust each other, come to a consensus about what information belongs on the blockchain and what does not. With the blockchain, each of us has a unique history of truth. Each of us has unique identifier that can be used to reach us on the blockchain without revealing our identities. Moreover, each of us has access to all of the information that exists. In this way, we can begin to rebuild a new economy. One who has trust at its foundation without needing to trust any individual person or business. Each of us has the ability to consider the information, and what that information is telling us as well as its impactions. Each of us can now behave as an individual and begin to contribute to the world around us without being limited by any one organization. Everyone can work together as well as individually to create value for one another. No single organization has a monopoly on the information the rest need to be able to contribute.”
After pausing for a moment, he looked at me and said: “The entire economy can now be built around the individual. Everyone can compete on a fair playing field and innovation will not be slowed. We can even use the blockchain to create a currency to pay each other directly for services. Imagine a world where you can be paid per word you write for a blog. Where you can be paid directly for developing a product and making it available to anyone in the world. If someone uses it once, they pay you, and only you, once. Everyone is incentivized to create. Everyone has access to the information they need to be able to create.”
At this point, my heart was beating so hard I could barely think. “Wait, but, where and huh?” Finally, I am able to stammer out: “How do we create the currency?” Simple, he replies, “we use the blockchain! There is only one puzzle left to solve: Double spending. See with a traditional currency, if I have a $20 bill, I cannot spend that same bill at two different places. However, when it comes to software, there exists this feature called copy-paste. How do we get around being able to copy and paste digital currency and spending that same unit of currency all over the place? This is called the double spend problem.”
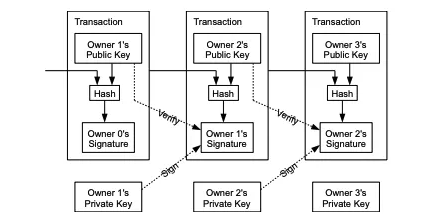
He continues his explanation by drawing a new diagram. “Let’s understand how a crypto currency transaction on the blockchain works with an example: Suppose Alice receives some crypto and wants to pay to Bob. How does she do it? Does she send tokens from her account to Bobs account? Well, no. There are no accounts, not in the traditional sense at least. Alice’s crypto exists on the blockchain. She alone possesses private keys that can be used to unlock ‘objects’ that have been signed over to her. So, when Alice wants to send Bob tokens, Alice first creates a new transaction. This transaction will have two components: Inputs and outputs. The key to how this pattern solves the double spending problem is that Alice’s transactions input can only spend the output of another transaction that has not yet been spent but has been signed over to her. How do we know if an output has not already been spent? Check the blockchain! Verify which transactions have inputs that spend the outputs of other transactions. All outputs that can be unlocked and spent by Alice’s input and that have not already been spent are called unspent transaction output (UTXO) and guarantee that only unspent outputs can be spent. This means that inputs spend the unspent outputs of transactions, and therefore those outputs cannot be double spent!
Once Alice’s inputs find the UTXO’s that satisfy how much she wants to send, she creates a new output that she locks with Bobs public key, in effect, signing it over to bob such that he may spend that output as an input of his own transaction. Since bob is the only one who has his private key, he is able to unlock that transaction and spend it himself.”
“But wait, you mentioned that we don’t have bank accounts in the traditional sense. What does that mean?” “Well”, he answered, “all of the information is stored on the blockchain. When you check your balance, what is really happening is that an algorithm runs through the blockchain looking for these UTXO’s. It then sums up the value of UTXO’s that have been signed over to you. This is your accounts balance! There are several ways of interacting with your balance. Keeping in mind that it all exists on the blockchain. These methods of interacting with your balance are called “wallets”.
There are three predominant types of wallets. The first is a full-service wallet. A full-service wallet performs three functions: It generates private keys, derives public keys and distributes those keys as required. The main advantage of these full-service wallets is ease of use. It requires no configuration and is ready out of the box. The main disadvantage being that they physically store private keys on a device which is connected to the internet.
The second, is a signing-only wallet. The main advantage of these types of wallets is that they are a more secure option. They store keys on a separate wallet program which is distinct for the networked device. These types of wallets have APIs that work with networked wallets to allow the user to sign for their transaction without needing to store the keys on the networked device. The main disadvantage is the loss of other capabilities.
The last is a hardware wallet. Hardware wallets take the concept of a signing-only wallet to the next level by creating a physical drive that is easy to carry and safely store. When the user needs to sign for a transaction, they pair the device with a networked wallet and sign by physically interacting with the device (usually pressing buttons). The main advantage to these types of wallets is improved security and the fact that they can easily be transported. The main disadvantage is that they can be easily lost. However, losing the device itself is not the end of the world as they are password protected and the private key can be recalculated by information only that user possess”.
What next?
At this point I am in shock. I can’t speak, but my mind is racing. I think to myself: He was right. I was not able to understand that back then. But I am starting to get it now. The blockchain gives us an immutable record that allows everyone to document their behaviour. It allows us to prove links between people, businesses and the consequences of their interactions. I think the economist George Gilder said it best when he noted that the ability of attestation is a critical advance that the blockchain offers. This is a new technology that is beginning to be used and will replace the existing system of the world. It will take advantage of everyone’s computers, phones, and distributed transaction, as well as their combined computing powers to offer unprecedented resources to the individual. According to Gilder “Blockchain technology will address the doldrums of centralization, insecurity, and sclerosis afflicting the current economy. […] The blockchain, ultimately corresponds to the reality of the world: The individual human mind, each with the ability to make its own contribution.”
While still in the process of thinking to myself, my dad adds, “If you remember, in your youth you often discussed the benefits of free. You said, the way we do business, spread ideas, cure disease is changing, and that the current system of the world that relies on free products by large businesses is what enables this. What you did not understand then, but understand now, is that we do not need individual organization which monopolize all the information of the world to achieve this. As a matter of fact, we can achieve more innovation, with better and cheaper products that contribute net benefits to the lives of others if we move past this old system and embrace a new system of the world. Privacy, security, quality and innovation should not be compromised for the sake of a free browser, a free email service or a free spreadsheet. People can work together and alone to build tools that add value to each other without comprising any of that. The current system of the world is incompatible with the needs of the world. At the heart of the new system, its ultimate resource, is not large businesses and free products that impose a centralized order; rather, it is the individual. The blockchain will empower individual human beings to create”.
Excited by the prospects I ask, “is there any chance we can build one to see what it looks like”? He answered, “how about you give it a try? See what you come up with! Here is my implementation for some inspiration”: https://github.com/mouradbenr/Blockchain
Bibliography
-
- Blockchain, (n.d.). Wikipedia.
- Bitcoin Developer Guide, (n.d.). Bitcoin.
- Bitcoin Developer Blockchain, (n.d.). Bitcoin.
- Bitcoin Developer Transactions, (n.d.). Bitcoin.
- Bitcoin Developer Wallets, (n.d.). Bitcoin.
- Blockchain Block Data, (n.d.). Wikipedia.
- Double-spending, (n.d.). Wikipedia.
- George Gilder: Life after Google: The fall of Big Data and the Rise of the Blockchain Economy. (2018)
- Hash function, (n.d.). Wikipedia.
- Merkle Tree diagram, (n.d.). Wikipedia.
- Liebkind, Joe, (Dec, 2020): Transaction Diagram, Investopedia.
